Your suppliers and vendors have an atrocious security posture.
Let me tell you about three incidents:
In 2013 Target was the target of a malicious hack which resulted in the loss of sensitive information like credit/debit card details, PINs, names, physical and email addresses, telephone numbers etc. of around 110mn customers!
In May 2015 the IRS admitted that copies of past tax returns of around 330,000 tax payers were stolen by a sophisticated gang of hackers.
In Aug 2015 nine suspected insider traders were arrested by the FBI on charges of committing securities fraud when they traded shares of companies like HP, Boeing, and Oracle based on advance financial information passed onto them by hackers.
In all the three cases core systems were not directly compromised by the cyber criminals. Instead, hackers took an easier route, selecting third party suppliers, vendors etc whose security controls were not up to snuff.
Why third party hacks are so easy
Here’s how the Target hack possibly went down
…the breach was likely to have been initiated through Fazio Mechanical Services (FSM), a heating, ventilation and air conditioning (HVAC) contractor that was connected to Target’s systems to provide electronic billing services, contract submissions and project management services…
FSM itself was the subject of an attack in which hackers stole the credentials required to breach Target…
By allowing FSM to connect to its internal networks, Target… effectively gave up some of its own security controls and entrusted them to a third party.
In the case of the IRS hack
The IRS…said hackers had used data from breaches of non-IRS sources to gain access to the agency’s Get Transcript feature from February to mid-May 2015 and harvested (330,000) records.
And finally in the insider trading case
The hackers … broke into the computer systems of PRNewswire Association, Marketwired and Business Wire (press release services).
Information stolen by the hackers is believed to have been used by their associates in the US to buy and sell shares of dozens of companies, including Boeing, Hewlett-Packard and Oracle, to make more than $30m in profit.
These three cases demonstrate that there are no guarantees that you won’t be attacked even if you have stringent security controls.
So long as your systems can be accessed by other third parties like partners, vendors or suppliers you will always run the risk of losing sensitive data and face the brunt of everything associated with a data breach.
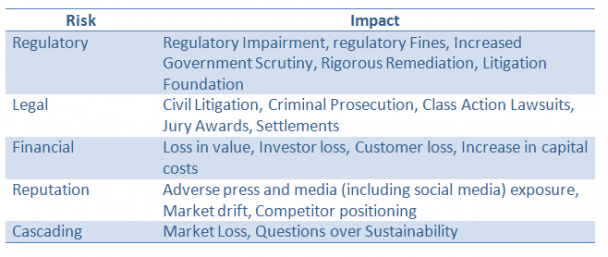
Negative impact of third party risk (Source)
The rot is not restricted to a few organizations though. According to a Booz Allen Hamilton report titled “5 Things about Third Party Risk Management”:
- Many organizations have no idea which third party contracts are active and what information they can access.
- They also don’t know what their most critical data assets are.
- Very few organizations manage third party and supply chain cyber risks on an ongoing basis, often with the result that low risk suppliers can become high risk after a period of time with no change in corresponding threat response.
The solution is to have a comprehensive risk management program that’s easy to set up and manage on a continuous basis without forking over truckloads of cash.
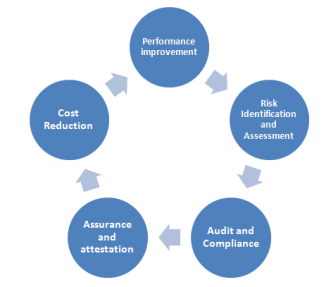
Elements of a successful third party risk management program
A third party risk management program looks like this
Elements of an effective third party risk management program
To implement a third party risk management program so that you can guard yourself against the contagious nature of IT risks do the following:
1) Add more teeth to your Business Associate Agreements
Set security policies that all third party vendors need to follow if their systems interface with yours and create contracts so that third parties are liable for any damages if any breach is traced back to their own IT systems.
2) Continuously review the security posture of contractors
You should institute a system of continuous monitoring to determine whether your suppliers are compliant with your standards, and whether there are any new threats or regulations that warrant a re-calibration of security requirements.
3) Share information
Join local and international information sharing and analysis centers set up to share information about hacks and threats. Cyber criminals often rely on hidden backdoors or zero day exploits to target systems and sooner the information is shared about an attack the less the chances are that the same hack can be repeated elsewhere.
4) Use data and technology
With AI increasingly being used in threat intelligence organizations can use algorithms to sift through big data related to supplier activity and flag abnormal behavior that might be a sign of a hack in progress. Using technology can also reduce costs and make executive sign in a no-brainer.
5) Training
Human error is still the most critical piece of the risk management puzzle. If users, both external and internal, are sensitized about data security the risks of attacks or data breaches can drastically fall.
Conclusion
When it comes to third party risk management it’s instructive to think of yourself as an automaker. Would you install a shoddily designed seat belt sourced from a third party supplier?
In an era of interconnected databases no organization is an impregnable fort and it takes just one loose brick somewhere for the bad guys to get in and wreak havoc. To safeguard yourself from attacks, help your partners guard themselves.